Introduction
Two of the greatest inventions, of the 20th century, were the telephone and the microchip. When these two inventions came together, it opened a whole new dimension for man to leave his mark. That dimension is better known as the internet, or at the global level, the World Wide Web. The rise of the internet is one of the biggest components that make this freshly emerging environment in the Information Age so dynamic. Businesses from the multi-national corporation level to the mom and pop restaurants have benefited from being able to be plugged into this information infrastructure. It was only natural because the internet offered dirt cheap marketing and advertising anywhere they could post a link. Another significant effect is that Print media has suffered do to the speed in which information can be disseminated. As the internet has affected business sphere and personal lives it has also transformed the battlefield.
Today, many of our military commanders and security advisers speak of Cyberwar, Netwar, and Cyber espionage as the major threats to our National Security. (Shactman, 2010) (Reid 2007) However, there seems to be little emphasis on psychological operations when speaking about cyber operations in comparison to cyber espionage and computer network attacks.
This paper will begin by introducing the reader to the discipline of Strategic Communication and then define the related terms Information Operations (IO) and Psychological Operations (PSYOPS). From there, I will construct a strategic environment by explaining some current threats and opportunities facing the United States on this battlefield. Using that information, I will explain the uses of PSYOPS and political warfare, and show some examples of opportunities that can be met with our own PSYOP effort in the internet realm.
Defining the realm of PSYOPS
To better understand PYSOPS, it would be best to look at the environment in which they reside. PSYOPS are a small part of a bigger set of operations called information operations. Information Operations are operations conducted under the discipline of strategic communication. According to the DOD strategic communication is defined as,
“focused United States Government efforts to understand and
engage key audiences to create, strengthen, or preserve conditions favorable for the
advancement of United States Government interests, policies, and objectives through
the use of coordinated programs, plans, themes, messages, and products synchronized
with the actions of all instruments of national power.” (United States 2009)
These efforts are coordinated and facilitated through a variety of means. They could come in the form of Public Diplomacy, Public Affairs, Operations Other Than War (OOTW), or direct military operations. If PSYOPS are involved, then it will most likely come in the form of OOTW and/ or direct military operations in the form of IO. The DOD defines information operations as,
“ The integrated employment of the core capabilities of electronic
warfare, computer network operations, psychological operations, military deception, and operations security, in concert with specified supporting and related capabilities, to
influence, disrupt, corrupt or usurp adversarial human and automated decision making
while protecting our own.” (United States, 2009)
From this definition, we can see that IO itself is made up of multiple components that are also conducted in concert with a larger message. At times, it can be hard to differentiate between them. For the interest of this paper, we will be focusing on PSYOPS branch of IO. The DOD defines PSYOPS as,
“Planned operations to convey selected information and
indicators to foreign audiences to influence their emotions, motives, objective
reasoning, and ultimately the behavior of foreign governments, organizations, groups,
and individuals. The purpose of psychological operations is to induce or reinforce
foreign attitudes and behavior favorable to the originator’s objectives.” (United States 2009)
Keeping this definition in mind, I will explain the threats and opportunities that could be made by utilizing our strengths and attending to our weaknesses.
Setting the Stage for the Strategic Environment
Although PSYOPS on the cyber battlefield are a less talked about subjects, it is not a new one. In February 2001, Major Angela Maria Lungu of the United States Army submitted a paper to the Naval War College titled The Internet and Psychological Operations. In her paper, Major Lungu noted three significant reasons for the growing popularity and need for PSYOPS on the internet. Those three trends were:
- A political method of prevention of violent outbreak
- Cross-border information regulation is near impossible
- Due to the global trends of urbanization and bias in international media gives almost limitless amount of ammunition to conduct PSYOPS (Lungu, 2001)
According to an interview with Admiral Michael Mullen that appeared on Wired.com’s Danger Room on April 21st 2010, the Admiral described the realities of the cyber threats and that “We’re being attacked today from other countries.” (Shactman, 2010) If America is under attack on this front who is attacking us and how are they doing it? Research shows that there is more than one entity that is engaging the United States on this front. From looking at some of our threats, we can get a sense for the commonalities and differences between styles of attack. With this understanding it would be possible to see where your threats and opportunities present themselves.
Russia
Due to the great amount of focus on Russia/ USSR in the latter half of the previous century, there are plenty of useful resources for researching Russia and their use of PSYOPS. Russia is no stranger to Psychological Operations and political warfare. During the Cold War the Soviet Union used PSYOPS to achieve their goals of subverting third world nations to help in their fight against the West. Defected KGB propagandist Yuri Bezmenov went into great amount of detail about the tactics used by Moscow during these times in a 1985 interview with Edward Griffin called “Soviet Subversion of the Free-World Press” and a video lecture series titled, “Deception was my job.” Bezmenov spoke of recruiting “useful idiots” (mostly sympathetic journalists, boozed up Western politicians, and anybody who could be duped into working for Russian interests) to disseminate Soviet propaganda and deliver “the party line” into American culture. (Griffin, 1985)
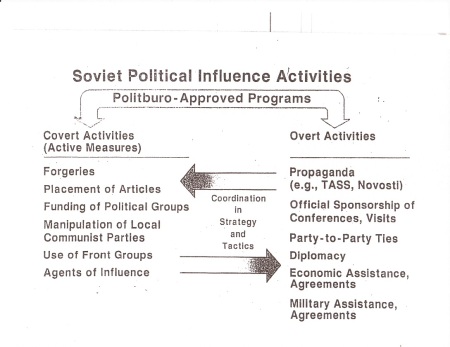
A class handout (see example 1) taken from the Dr. J Michael Waller’s (Dr. Waller is a Professor of propaganda, public diplomacy, and political warfare class at The Institute of World Politics) propaganda class blog. Example 1 refers to the old USSR/ Russian methodology of Information Operations and their use of PSYOPS. Example also serves as a great visual for summarizing the methodology of soviet “influence activities” that Bezmenov spoke of in the videos. From examining example 1, we can see that their PSYOPS were Politburo approved and divided into two categories, covert activities (or commonly referred to as, active measures) and overt activities. Under this split each group took on a number of roles and tasks while coordinating strategy and tactics. Yuri describes this to be a very effective strategy. It is not clear if this strategy’s success is due to the authoritative rule of the Soviet government over their agents. None the less, these methods will be important to keep in mind.
Although times have changed and the USSR is no more, some experts and journalist seem to be seeing the onsets of a resurgent Russian Bear awakening from hibernation. Would an indicator be seen in a renewed effort of a new form of “active measures”? Some experts and news columnist have thought about that as well. (Waller, 2010) (Schuster 2010)
On April 15th, the permanent Head of NATO to Russia, Dimitry Rogozin posted this message on Twitter: “New breakthrough article by James Jatras in the Washington Times http://adresno.ru/JnQCQ .” (Rogozin, 2010) The article itself seems harmless and speaks of US relations with Russia. However, this article was not a legitimate Washington Times article. The supposed article by James Jatras was nowhere to be found when searching for it on Washington Times’ webpage to find its authenticity. Referring back to Example 1, it can be noted that forgeries and placement of articles are on the top of list for Active Measures. At this time the article in question has not been verified. So what would be the point of taking all these efforts?
“According to my opinion and the opinion of many defectors of my caliber, only about 15% of time, money, and man power go towards espionage, the other 85% is a slow process which we call either ideological subversion or active measures… or psychological warfare. What it basically means is to change the perception of reality of every American to such an extent that despite of the abundance of information no one is able to come to sensible conclusions in the interest of defending themselves, their families, their community, and their country its great brain washing process in goes very slow and its divided into 4 basic stages.” – Yuri Bezmenov (Griffin, 1985)
Bezmenov went on to emphasize on these stages. The first stage is called, demoralization, a process that takes 15-20 years. This was the determined time that it would take to educate the enemy’s youngest generation under the subverter’s ideology. The second stage is called, destabilization, a process that takes 2-5 years. In this process the subverter will take control over economic policy, defense policy, and foreign relations.” The next stage is the crisis which could only take 6 weeks to bring a nation to a crisis. Later, I will illustrate on how that time may be shorter than expected in the Information Age. The final stage (after the violent coup has taken place) is a period called, normalization. Bezmenov said the term was a “cynical expression that was taken from Soviet propaganda.” The term originated from announcement by a Soviet leader when he had announced that the situation in Czechoslovakia had “normalized” when Russian tanks entered the country in 1968. (Griffin, 1985)
It may not be about ideology with the Russians anymore; however, Russian national interests remain. The use of forged news stories should be looked at and scrutinized closely to see what results they would benefit from these “articles.” Judging by their current actions, the statement Yetlsin made concerning the changes to the old Cheka security apparatus as being proved “unreformable” and “superficial and Cosmetic”, and the fact that we appears to be a new rise in “active measures” should give rise to concern. (Berman, & Waller, 2006) (Rogozin, 2010) (Schuster, 2010)
Iran
While PSYOP activities between the United States and Iran remain closely guarded secrets. Iran has clearly demonstrated the opportunities and threats the internet offers in warfare. (Nasr, 2009)
The Iranian elections of 2009 proved to be an eye opener to many in the mainstream media and to any student of political warfare. It was the first time an international dispute, what seems to be a coup in the making, was covered in great detail on social networking sites (i.e. Twitter, YouTube, and Facebook) with almost instant reporting via mainstream media. (Nasr, 2009) Members of Iran’s Green Party were able to appeal to the world through the internet for what they feel was a rigged election. (Nasr 2009) The significance of this was huge because the Iranian government was not able to silence the voice of opposition despite the efforts. The Iranian Green Movement was also able to gain international support, and they got it. International supporters of regime change in Iran were able to set up proxies, to bypass security measures, on the internet infrastructure taken by the Iranian government and the Iranian Revolutionary Guard. (Austin Heap, 2009) They also received literature in nonviolent revolution and protest. (Waller 2010)
From this evidence, we can note that the Iranian Green Movement has clearly shined the light on the potential power of these social networking sights. If one can appeal for help, then that help may come with strings attached or in a form that may manipulate the way their policy is decided. The internet could be a great way to influence the minds of a target nation, not only in hopes of pushing American interest there but also to disrupt enemy plans and goals.
Global War on Terror
The Cold War and Global War on Terror (GWOT) have something in common. At the root of all our problems are ideological extremists with a willingness to kill the rest of the world to achieve their goal of world power, at the expense of forcing their ideologies on the masses. So it should really be looked at as a — War of Ideas– that we are facing, rather than a select few radicals armed with ak47s and explosive vests. Wars will be fought with all sorts of weapons, but they will start and end only with ideas and ideologies, all of which is rooted in information.
The Taliban have understood the need to conduct PSYOPS of their own. Strategy Page ran a story about a group of Taliban insurgents who were caught in the act of burning Qurans, so that they may frame US Marines as being highly disrespectful of Islam and Muslims. (Strategy Page, 2010) There have been other stories about the Taliban manipulating photos of the dead after a US offensive. A Marine Corps Staff Sergeant explained that the Taliban a field-to-net tactic to create an ugly image of Americans, in order to incite hate towards our forces and delegitimize our presence. That tactic was to add more dead bodies to the scene and confiscate weapons before the press could arrive on the scene. This was done to make the scene look as if Americans obliterated an unarmed mass of people. He added, the Taliban would not only try to quickly get this message to journalists, but they would also quickly release the images on the World Wide Web, as a means to through the first informational punch. (Farnes 2009)
Dr. J Michael Waller wrote extensively about using strategic communication in the GWOT in his book is called, Fighting the War of Ideas like a Real War. In this book, Dr. Waller laid out his plan to fighting this War of Ideas. This book can be summarized by this quote:
“In order to develop successful wartime messages, we must know first what we seek to accomplish and how we wish to achieve it. If we want to win a longer-term global war, then we must secure and maintain a strategic influence presence around the world to support not only the current conflict, but other issues, present and future.” (Waller, 2007)
Therefore, the emphasis (in the GWOT) should not be in forgeries or fake news stories, but in a strategically placed and constructed messages that account for the cultural sensitivities, norms, mores, and specific interest of the target area. (Waller, 2007)
Dr. Waller stated that this method started with dividing the opposition. This was to be done by attacking the semantics of rhetoric coming from an ideological enemy. (Waller, 2007) The understanding is that not all people will feel the same exact way even if they follow the same scripture; therefore, we could play off these slight differences by controlling the dialogue in favor of United States interest.
For instance, Waller names three different groups of Muslims that have different views of jihad. (Waller, 2007) For simplicity purposes, I will name two of them. First, there are the moderate Muslims that tend to roll with the definition of “jihad” as somewhat of a peaceful movement within one’s own life to serve Allah. The second group, is the Islamic conservatives/ radicals/ fundamentalists who tend to believe that jihad is not only a spiritual war for the betterment of one’s self, but also see it as a reason to engage in physical violent war for the Islamic conquest of the world. These fundamentalist are so out of touch, they are willing to drive a truck next to a group of young Afghan students leaving their school house and detonate a bomb that would kill himself and the group of children in an explosion, in the name of an Islamic state. (Waller, 2007) (Kahn, & Oppel, 2010) Their almost appear to be polar opposites.
Here is where the tactics of using semantics enter into play in the dialogue of the extremists which is to be taken away and substituted for the moderate interpretation by simply relabeling the enemy. (Waller, 2007)
The root of the word jihad is derived from jahada. Jaahda, which comes from the notion of a moral struggle for self-betterment. (Waller, 2007) While we in America deliver the message of killing jihadists we inadvertently weaken our support amongst the crowd we want to dissuade from joining the ranks of the fundamentalists. These extremists are mass murdering psychopaths and should be referred to as such, instead of as individuals out for self-betterment they shall be known as individuals guilty of hirabah. Hirabah is rooted in the words of anger, war, and fighting. (Waller, 2007)Knowing this, the US should craft its messages so that every word will have the residual effects that would further isolate the enemy.
This is where Waller’s 2nd stage comes from, that is isolating the enemy. This is done by using the new dialogue to undermine the old one used by the extremists. According to Abdul Hakim, a University of Michigan Professor, “Hirabah… is the most severely punished crime in Islam, carrying mandatory criminal sanctions.” (Waller, 2007)
From here we can see the difference in which the context of these words can be used and understood. If extremist are going to lie and claim themselves as individuals out to represent a “Religion of Peace”, but then go around killing the innocent, than we shall call them for what they are, bloody thirsty maniacs out for a fight. If this group could be found guilty of “the most severely punished crime in Islam”, than it would have a huge impact amongst the Islamic community. Not only does this release us from the grip of enemy dialogue but it will also bring up the chance for Islam to take care of itself, which in the end is what it will take. (Waller, 2007)
Waller didn’t stop there; he went on how to further isolate the enemy through ridicule and how it is a vulnerability found in the characteristics of dictators and tyrants. (Waller, 2007)He also believed that through ridicule and laughter by the enemies peers that the tyrant will be not only feel uncomfortable to rhetoric he cannot counter, but it would also lead the tyrant to make a pivotal mistake that could be hit on to make things worse for the enemy. (Waller, 2007)
Seeing as how our enemy in the Global War on Terror has already began conducting PSYOPS and PSYOPS in the internet realm to shape their own image of America and themselves, we must confront the threat wherever it may be. Dr. Michael Waller lays out a very persuasive strategy for Fighting the War of Ideas. These ideas worked into PSYOPS conducted on extremists’ message boards and social networks could prove to be that spark needed to re-rally support for the war effort and undermining our enemy.
China
There are a plethora of open source documents and news article that can articulate China’s strategic interest in the internet. Although much of the information concerning China and Information Operations has to do with Computer Network Operations (CNO) and Cyber Espionage there is plenty of data to look at the example of the Chinese approach to PSYOPS in the internet arena. (Reid, 2007)
According to the September 15th testimony of James C Mulvenon, Ph.D. Director of
Advanced Studies and Analysis at the DGI Center for Intelligence Research and Analysis, before the U.S.-China Economic and Security Review Commission in a hearing called, “China’s Military Modernization and the Cross-Strait Balance”, which was compiled into a report titled “Chinese Information Operations Strategies in a Taiwan Contingency” stated the methodology to Chinese IO was to first size up the enemy, and then exploit their weakness. (Mulvenon 2005)
The report notes multiple weakness or vulnerabilities that the PLA could exploit. For example, the Chinese believe the island of Taiwan is information dependent and any threat to their communication infrastructure will have severe economic backlash. (Mulvenon 2005)The second weakness that the Chinese saw was that the Taiwanese did not have the stomach for violence and any threat of violence would trigger fear and panic) (Mulvenon 2005)These two weakness alone were enough for China to begin conducting PSYOPS on the internet. Mulvenon shared an example; a rumor that started on the internet resulted in the Taiwanese stock market dropping two percent in just four hours. How was this possible? The rumor was about the Chinese military shooting down a Taiwanese plane. The fear and panic (of more violence towards the people and disruption of the infrastructure) spread so fast it affected the market within a matter of hours.
This testimony gave great insight on Chinese strategist. The report noted many reasons for their use of IO. The most significant reason was that IO allows for their influence to extend well beyond their military’s capability and that it offers plausible deniability of nearly all operations. (Mulvenon 2005)
Mulvenon noted 5 key features of the Information Warfare strategy towards the US:
- China emphasizes defense, where as they would attack America for our “fetish for the offensive.”
- Information Warfare is used as a weapon in the initial stages of conflict
- IW will allow the Chinese to win an information campaign without having to use conventional military tactics.
- The United States is information dependent
- Computer network attacks are preemptive weapons. (Mulvenon 2005)
This sizing up not only allows one to see the threats America faces in conflict with China, but it also gives us the opportunity to know where American efforts need to be directed. None the less, we can see that China has a lot of interest in internet-based operations. Their use of PSYOPS to wreak havoc on Taiwan’s economy is a good example to show the Chinese are already engaged in online PSYOPS.
Conclusions of the Strategic Environment
Information in warfare has always been instrumental. Sun Tzu was a Chinese strategist in 500bc that understood the importance of information and deception. Today, America faces these threats in multiple arenas. If an enemy is going to attack America and attempt to destroy our way of life and Constitution, than America should face it’s aggressor down anywhere it shows its face. These different forms of attack are going to each need their own plan but each will need to be a part of a well orchestrated message.
Defense Policy and Policy of PSYOPS
There is no definite line that is drawn in the sand that defines at what point the military would be used in conducting or countering enemy PSYOPS. As we move into the Information Age the lines between operations and the means in which we engage will most likely be ever changing, as is the battle field.
Currently the only legislation that really points at IO is the Smith-Mundt Act. The act essentially says that any information broadcast outside of US borders cannot be disseminated within US border. With the blurring lines of information operations, the increase in technologies, and what seems to be an archaic policy leave the potential applications in the air. (Armstrong 2009)
Force Structure of Online PSYOPS
Currently, there is talk of a new US Cyber Command that is to be headed up by Lieutenant General Keith Alexander. (Shactman, 2010) This cyber command is facilitates cyber operations for US Strategic Command. As of right now, each branch of the military (and the alphabet agencies) have their own PSYOP department. According to a rumor floating around amongst Airmen in the United States Air Force (USAF), it will be the USAF that will take lead of the Joint Task force for Cyber operations. It remains unknown (about how many of these operations will be of the influence nature. However, for these type of influence operations to be successful and reinforced, coordination between the intelligence community, the military, the business (domestic and international), and non-governmental organizations to achieve a unified strategy that achieve our objectives and goals.
Acquisitions, Research and Development, and Procurement
A big advantage of cyber PSYOPS is that the operations require very little and they are very cheap to conduct. All that is needed is an agenda, a device with internet access, and someone to push that agenda on to that has internet access too. However, an effective PSYOP should have a good amount of area knowledge in which the PSYOP is to be conducted. A failed PSYOP could have adverse effects on US efforts.
Conclusion
Topics for future research include propaganda, public diplomacy/ affairs, strategic communication, and counter subversion methods. If PSYOPS will be used there must be a way to preserve truth and remain consistent, while still holding on to our freedom. Truth and consistency go hand-in-hand. The message must be just as clear inside our borders as we broadcast it outside of our borders. It is under my belief, that if a country cannot have a clear message at home and a clear message abroad corruption from either side will lead it to failure.
The possibilities in cyber PSYOPS are dynamic. They could be used to sway the decisions of policy makers as is the case of Iran where political dissidents used the internet to appeal for and got international help to fight against their corrupt regime. PSYOPS could be used as part of a preemptive attack before sending in conventional force as in the Chinese strategist see it. For instance, we could use cyber PSYOPS as a form of military deception. For example, we could flood the inboxes, social networking sites, and influential message boards of a pending attack in a city in order to divert attention from another offensive operation in more strategic area to catch the enemy off guard. Cyber PSYOPS could also be used as an efficient means to overload a country with biased information that tempts groups of regime change into destabilizing a country.
This report provides only a small view of the strategic environment surrounding America. Multiple nations appear to have a cyber PSYOP offensive strategy to engage the United States for a multitude of reasons, which could be anything from swaying policy makers to flooding the net with content to eat away at the morale of a populous. If our primary adversaries are already engaging in these operations it would make absolute sense to counter their efforts with efforts of our own.
Work Cited
Armstrong, M. (2009). The Report on the smith-mundt symposium. Proceedings of the Smith-Mundt Symposium, www.moutainrunner.us/symposium
Austin Heap, Initials. (2009, June 15). How to Setup a proxy for iran citizens (for windows!) [Online Forum Comment]. Retrieved from http://blog.austinheap.com/how-to-setup-a-proxy-for-iran-citizens-for-windows/
Berman, I, & Waller, JM. (2006). Dismantling tyranny: transitioning beyond totalitarian regimes. Lanham: The Rowman & Littlefield Publishing Group, Inc.
Farnes, Jay Staff Sergeant USMC “Guided discussion on nature of the enemy” Marine Corps Recruiting Depot, San Diego, CA. February 2009
Griffin, GE. (Producer). (1985). Deception was my job the testimony of Yuri Bezmenov, KGB
propagandist. [Web]. Retrieved from http://www.youtube.com/watch?v=CLsi0Ialvxk
Lungu, AM. (2001). The Internet and Psychological Operations. Retrieved (2010, April 20) from http://www.dtic.mil/doctrine/jel/jfq_pubs/0628.pdf
Kahn, I, & Oppel, R. (2010, January 1). Taliban truck bomb punishes pakistani villagers. Retrieved from http://seattletimes.nwsource.com/html/nationworld/2010668765_pak02.html
Mulvenon, J. (2005). Chinese informationation operations strategies in taiwan. Proceedings of the China’s military mondernization and the cross-straight balance, http://www.uscc.gov/hearings/2005hearings/written_testimonies/05_09_15wrts/mulvenon_james.php
Nasr, O. (2009, June 15). Tear gas and twitter: iranians take their protests online. Retrieved from http://www.cnn.com/2009/WORLD/meast/06/14/iran.protests.twitter/index.html
Reid, T. (2007, September 8). China’s cyber army is preparing to march on america, says pentagon. Times Online, Retrieved from http://technology.timesonline.co.uk/tol/news/tech_and_web/the_web/article2409865.ece
Rogozin, D. (2010, April 15). New breakthrough article by james jatras in the washington times [Online Forum Comment]. Retrieved from http://www.twitter.com/rogozin
Russian Front, Initials. (201, April 12). Host url for russian news forgeries. Retrieved from www.advstage.washingtontimes.com
Schuster, s. (2010, April 8). Kyrgyzstan uprising: did moscow subvert a u.s. ally?. Time AP press release, Retrieved from http://news.yahoo.com/s/time/20100408/wl_time/08599197859000
Shactman, N. (2010, April 21). Top officer fears cyberwwar, hearts karzai, tweets with help. Wired Magazine,Retrieved from http://www.wired.com/dangerroom/2010/04/top-officer-fears-cyberwar-hearts-karzai-tweets-with-help/ (Shactman, 2010)
Strategy Page, Initials. (2010, February 15). U.s. troops in marjah threatened by lawyers . Retrieved from http://www.strategypage.com/htmw/htiw/articles/20100215.aspx
United States (2001 (Amended through Oct 31 2009)). Department of Defense Dictionary of Military and Associated Terms: Joint punblication 1-02 Field, Washington, DC: Headquarters, Department. of Defense.
Waller, JM. (n.d.). Example 1. Soviet political influence activities. Unpublished raw data, Propaganda, Institute of World Politics, Washington, D.C.. Retrieved from http://jmw.typepad.com/propaganda_course/
Waller, JM. (2007). Fightingthe war of ideas like a real war. Washington: The Institute of World Politics Press.
Waller, JM. (2010, February 07). http://jmw.typepad.com/political_warfare/2010/02/serbian-nonviolent-action-manual-can-be-useful-for-iranian-resistance.html [Web log message]. Retrieved from serbiannonviolentactionmanual
Waller, JM. (2010, April 07). Kyrgyzstan revolution: hopeful repercussions for Iran?. Retrieved from http://jmw.typepad.com/political_warfare/2010/04/kyrgyzstan-revolution-hopeful-repercussions-for-iran.html

Here is the string of research on that Rogozin link. Very weird. I can’t seem to find the original article from Washington Times. (If there ever was one.) I wonder if James Jatras wrote this? I have many more questions too…. Maybe I am missing something? This is what I got.
From: http://www.twitter.com/Rogozin
“New breakthrough article by James Jatras in the Washington Times http://adresno.ru/JnQCQ about 1 hour ago via web”
Interesting that news story is an image and not text. Hmmm. You dont see that often very much.
Search Results for James Jatras on Washington Times’ website: http://www.washingtontimes.com/search/?cx=015385541671335030271%3Anfb7f1nj88q&cof=FORID%3A11&ie=UTF-8&q=James+Jatras&sa=Search&siteurl=www.washingtontimes.com%2Fnews%2Fsecurity%2F
Only 2 mentions and neither of them are that story.
The image address for that picture is weird….
Actual Url for the link: http://advstage.washingtontimes.com/timeforamerica.html
Actual Url of the image: http://advstage.washingtontimes.com/images/timeforamerica.jpg
Interesting. “It Works!” http://advstage.washingtontimes.com/
Google Results of ‘advstage.washingtontime’s: http://www.google.com/search?hl=en&client=firefox-a&hs=ih5&rls=org.mozilla:en-US:official&q=advstage.washingtontimes&start=10&sa=N
(I wonder if I can get a free trip if I send fill this out and send it in….http://advstage.washingtontimes.com/files/trips/StKittsReply.pdf)
Hmmm is it me or is there a Russian trend in the search results?
Who is James Jatras?
Bio: http://www.ssd.com/jjatras/
Here is one of his papers: http://www.srpska-mreza.com/nwo/JGJatras-97.html
That is a weird site for that paper to be attached to… http://www.srpska-mreza.com/
His name gets around the Orthodox Church: http://www.orthodoxytoday.org/articles8/Jatras-Independent-Kosovo-A-Threat-Not-A-Country.php
Stella Jatras (mother of James): http://www.krokeai.com/Krokeates/Professions/Jatras/Stella%20Jatras.htm
Political Contributions? Of course: http://www.campaignmoney.com/political/contributions/james-jatras.asp?cycle=08
So Squire, Sanders, and Dempsey have a PAC, eh? http://www.campaignmoney.com/political/committees/squire-sanders-and-dempsey-llp-political-action-committee-squire-sanders-pac.asp?cycle=08
Hmmm a $1000 donation to Sherrod Brown. Daughter Emily Brown is an organizer at SEIU: http://www.muckety.com/Sherrod-Brown/1494.muckety There are other characters on the list of campaign contribution recipients.
Differences in the pages:
the buttons on top of the “alleged” news article links go to different places.
“News” button on Real Webpage URL: http://www.washingtontimes.com/news/
“News” button on Fake Webpage URL: http://advstage.washingtontimes.com/timeforamerica.html#
There rest of the buttons (when clicked) lead to the fake news article (not if you use the menu underneath it, that links back to the real washingtontimes.com). The only section that doesnt is the “communities” section.
They have also cleverly add “US News | National Security | Bookmark This Page | Events & Places” to make it appear that you are being linked to a section of the Washington Times that has to do with National Security to recreate a feeling of legitimacy.
The effects of these documents: http://www.pakistantalk.com/forums/archive/index.php/t-5050.html
Anybody?
[…] the James Jatras research string of a questionable webpage article from the Washington Post in the Psychological Operations in the Information Age posting. (See the comment section). The folks at the Foreign Policy Magazine, seem to play this off as a […]
Uh oh… you are using a very old definition of Information Operations. Please look up the SECDEF Memorandum, dated 5 January 2011, entitled “Strategic Communication and Information Operations Memorandum”. If I had your email I could send it to you..
Reblogged this on darkwingwren.